As digitalization progresses, industrial equipment platforms are shifting to a combination of general-purpose devices and general-purpose OS, and it has become commonplace for them to be connected to networks using general-purpose protocols. On the other hand, the diversification of cyber attacks has led to an increase in the number of cases where industrial equipment is targeted, and there is a movement to make security measures mandatory. Please take advantage of Contec's device security solutions that solve issues specific to industrial equipment.
Products equipped with allow list security software
Trellix Embedded Control
With Contec, you can start with a single industrial computer with Trellix (formerly McAfee) Embedded Control.
We have delivered many projects including IoT gateways, money processors, and extending the life of legacy OS equipment. Let us help you implement allow list security software with Trellix Embedded Control.
Contact Us
Industrial Equipment Security Risks
Open Industrial Equipment
With the advancement of IoT, are you using open technologies and general-purpose OSs without taking security measures? Are you connecting industrial equipment to IT networks?
Diversification of Cyber Attacks
Did you know that industrial equipment is increasingly being targeted due to the diversification of cyber attacks, including financial and intellectual property theft and hacktivism (social and political protest)?
Obligation and Legalization of Countermeasures
Did you know that security standards and guidelines are being established and security measures are being required across industries and supply chains?
Examples of Industrial Equipment Targeted

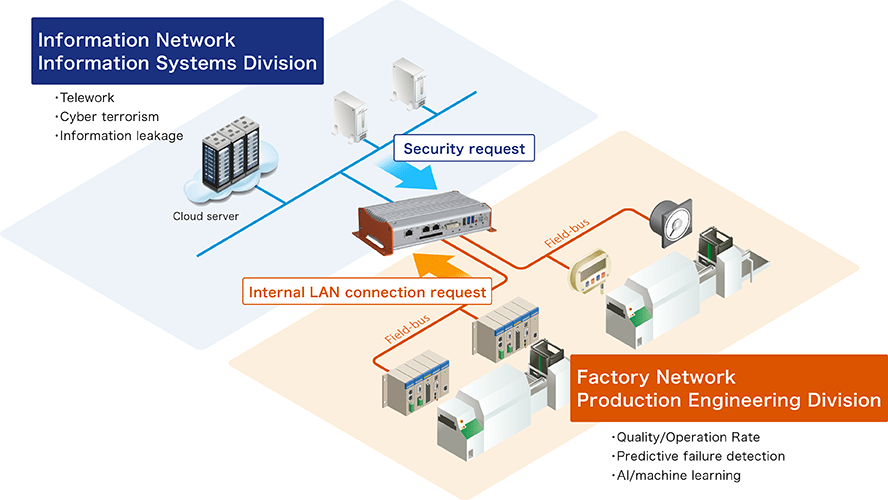
Balancing Factory Productivity and Security Security
Measures Suitable for OT Networks
Robust security measures are essential to protect the expanding network from cyber attacks. However, the information systems division in charge of the information technology (IT) network prioritizes the level of security measures, while the production technology division in charge of the operational technology (OT) network prioritizes stable operation and improved productivity. Security measures are prioritized differently within a company, and solutions are required to meet these priorities.
Benefits of Trellix Embedded Control
Trellix (formerly McAfee) Embedded Control is the leading allow list endpoint security software in industrial equipment. It solves many of the challenges faced in securing industrial equipment.
Minimize impact on
resource performance

- Number of CPU load percent
- No need for periodic system scans
- No need for pattern file updates
Extend the life of hard-to-
migrate legacy OS systems

- Allow list type
- Compatible with Windows XP/7 and other older operating systems
- Compatible with Windows Server/Linux
For hard-to-manage
distributed systems

- Supports standalone environments
- No internet connection required
- Maintenance free
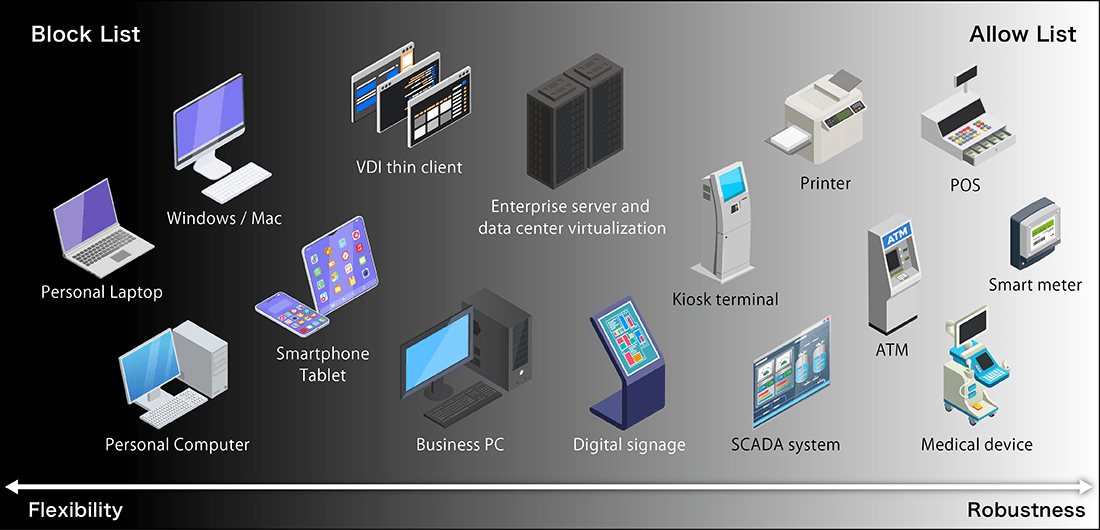
What is the Allow List Method?
- Only safe files registered in the list are allowed to run. Infiltrating malware is blocked because it is not registered in the list.
- Prevents infection from known malware as well as unknown malware that will emerge in the future.
- Blocks unauthorized application changes by users and unauthorized changes to devices.
Dominant share in industrial equipment because it is more robust than block list methods and can be used in standalone environments
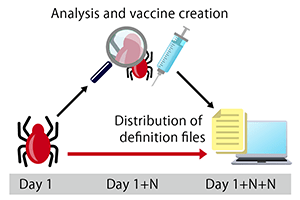
What is the block list method?
The block list method is anti-virus software that checks whether a virus is detected by pattern matching. Be careful when using it with industrial equipment.
Unknown threats (zero-day attacks) Attacks targeting OS vulnerabilities
CPU and memory burden of periodic scans Increase in definition files
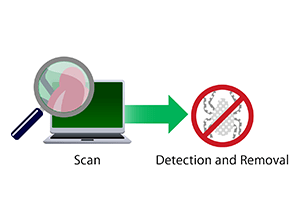
Definition file management, operational costs of deployment

Trellix Embedded Control, a standard product of Allow List type security software
With Contec, you can start with a single industrial computer with Trellix (formerly McAfee) Embedded Control.
We have delivered many projects including IoT gateways, money processors, and extending the life of legacy OS equipment. Let us help you implement allow list security software with Trellix Embedded Control.
Contact Us